X-Download-Options
X-Download-Options
Cookie Theft Example
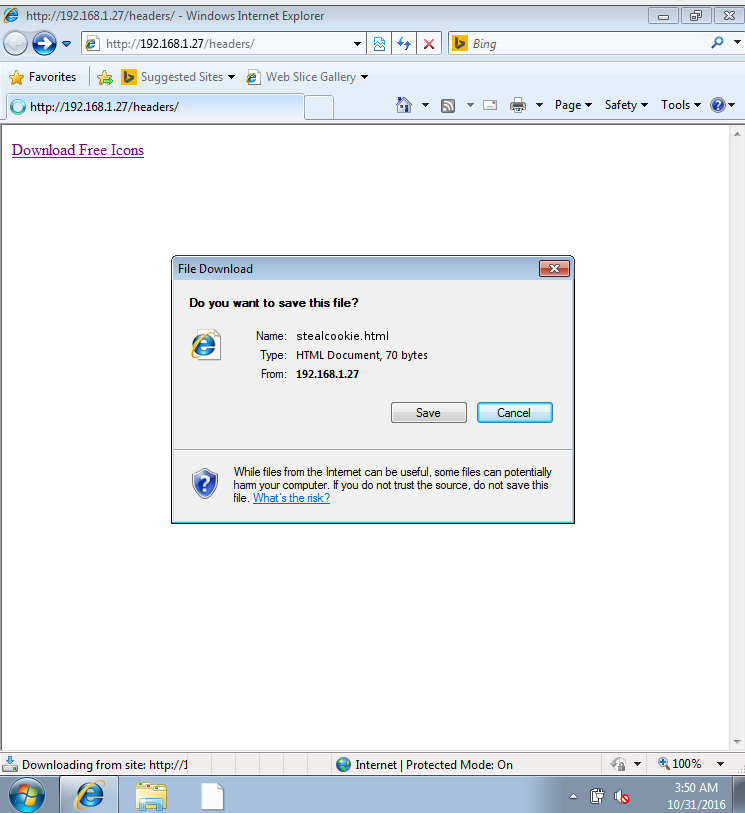
Let’s imagine a user uploads a file called stealcookie.html to our website. You can use the below header to force the file to be downloaded instead of executed:
Though even if we force the download, the user will still be prompted to decide if he or she should download the file or open the file. If the user opts to open the file, the malicious code will be executed.
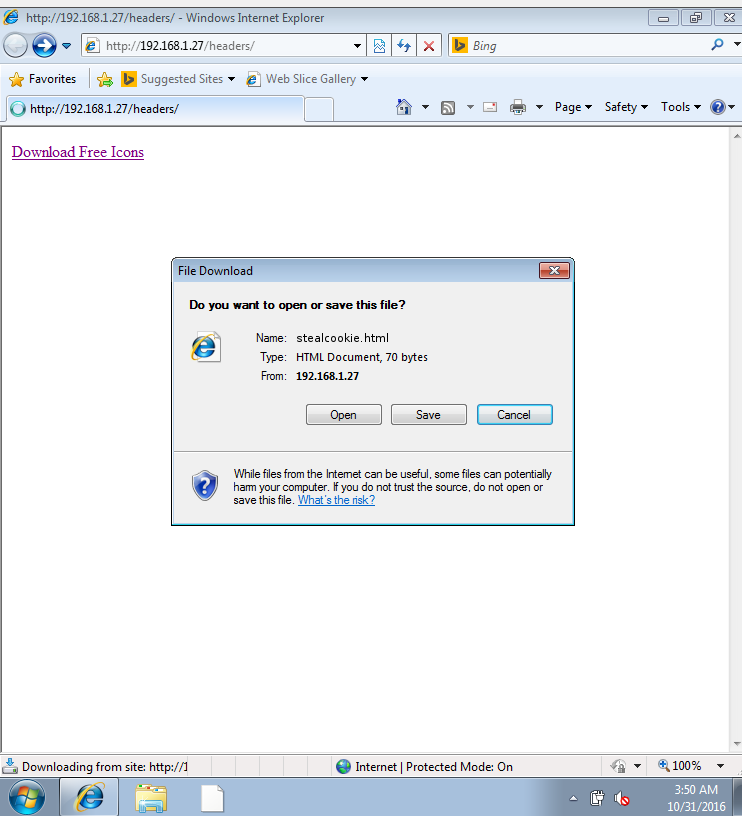
If the user clicks Open, the file would be parsed by the browser and displayed on our website, enabling the malicious code in the file to access all other pages on the same domain.
The only way to prevent this is to remove the option the user has to open the file by adding the noopen directive to X-Download-Options HTTP header:
When this directive is used, the user can still save and open the file, but this way the malicious code will be prevented from running on our website. Though it will run on the user’s file system.