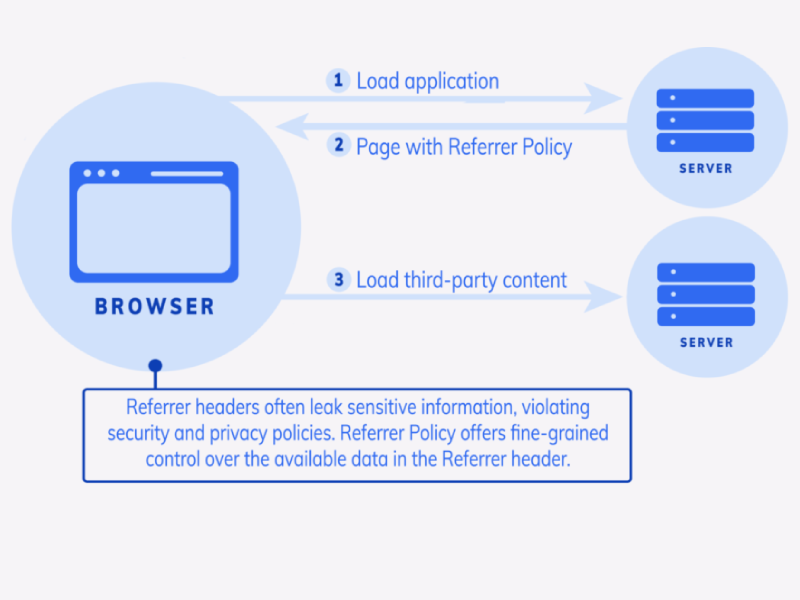
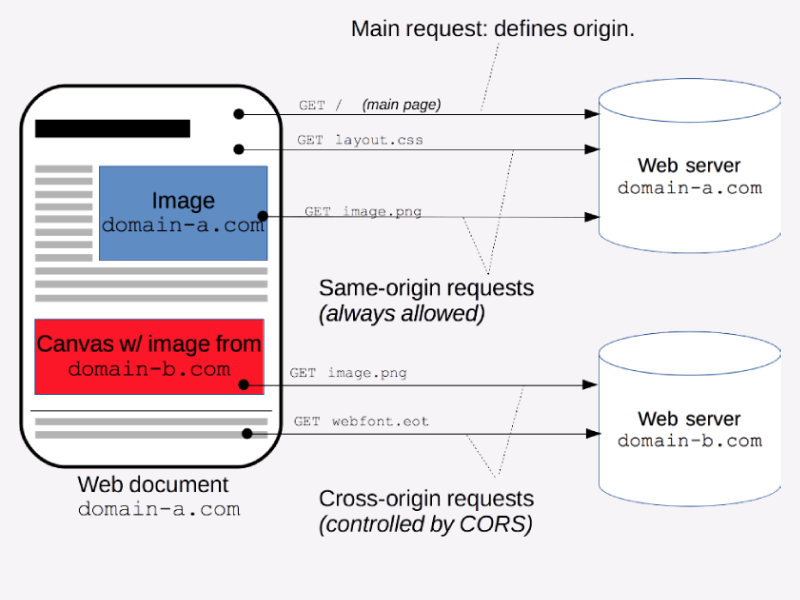
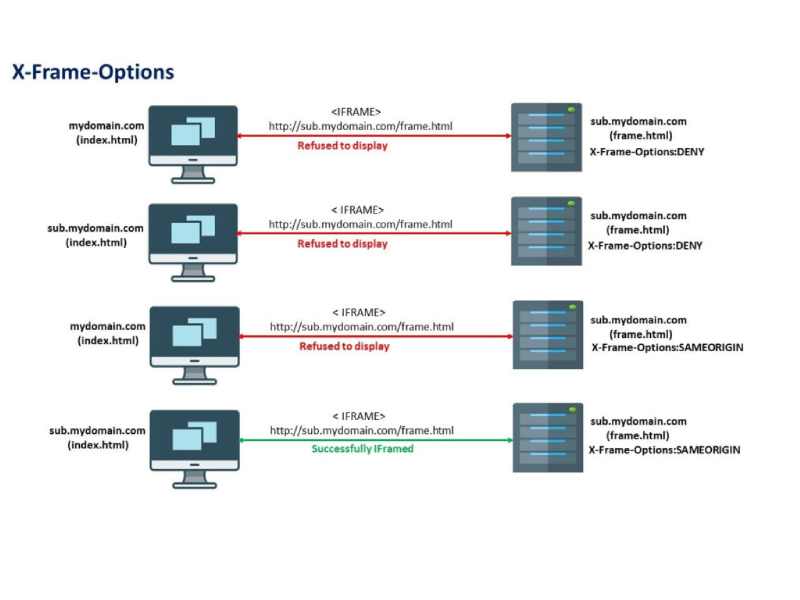
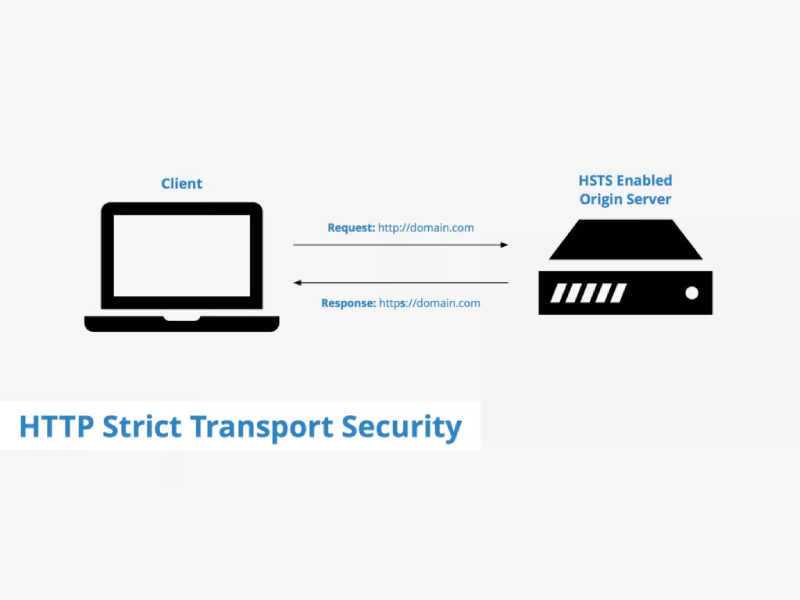
Secure Your WordPress Website with Regular Updates and Measures
In today’s fast-paced digital world, maintaining a secure and up-to-date WordPress website is crucial for its success and longevity. With the prevalence of cyber threats and evolving technologies, keeping your site in optimal condition is not just a best practice but a necessity. In this article, we’ll explore smart ways to ensure your WordPress website […]
Secure Your WordPress Website with Regular Updates and Measures Read More »